Featured
Table of Contents
What Is Openvpn? - Review
Still, it deserves pointing out that SSTP is natively constructed into Windows platforms, so it's much easier to set up than Open, VPN. In general, both Open, VPN and SSTP are a decent choice, but Open, VPN is merely more effective. In case you 'd like to discover more about SSTP, examine out this article.
It's safe to say that both Open, VPN and Soft, Ether are truly safe procedures. They're open-source, utilize military-grade ciphers like AES, make use of 256-bit encryption, and likewise utilize SSL 3. The main difference in between them is the age Soft, Ether is much more recent than Open, VPN.
In terms of speed, Soft, Ether fares much better than Open, VPN. In fact, according to the research from the University of Tsukuba (individuals behind Soft, Ether VPN, so not a 100% subjective source), the Soft, Ether procedure is expected to be 13 times faster than the Open, VPN protocol.
What Vpn Protocols Does Privadovpn Utilize?
You ought to understand that even if you use a VPN company who uses Soft, Ether connection, you'll still require to download additional software for it to run. With Open, VPN, that's optional. Like Open, VPN, Soft, Ether can also run its own server, but the Soft, Ether server can actually run the Open, VPN protocol, along with other protocols like IPSec, L2TP/IPSec, SSTP, and Soft, Ether.
In the end, Soft, Ether is a solid Open, VPN alternative. If for whatever reason you can't utilize Open, VPN, you ought to try Soft, Ether. If you 'd like to understand more about it, follow this link. For beginners, PPTP is substantially weaker than Open, VPN in terms of security. While Open, VPN can deal with 256-bit file encryption secrets and ciphers like AES, PPTP can only use 128-bit secrets through the MPPE cipher.
Though, you need to be more mindful with IPSec when configuring it, because a small mistake can ruin the defense it uses. Likewise, considering that IPSec inhabits kernel area (the area on the device reserved for the os), its security can be limited by the way it's configured by the supplier.
What Is Openvpn And How Does Openvpn Work?
Still, you must know that IPSec might take longer to work out the tunnel than Open, VPN does. Interested in finding out more about IPSec? Inspect out this short article. Open, VPN and IKEv2 are both safe procedures, however it's worth noting that Open, VPN uses TLS/SSL to secure information at the Transportation level, while IKEv2 protects data at the IP level.
And while IKEv2 was established by Cisco together with Microsoft, that's not such a substantial concern given that there are open-source implementations of IKEv2. Open, VPN offers more assistance when it comes to cross-platform compatibility, however IKEv2 is usually a favorite of mobile users since it's natively incorporated into Black, Berry devices.
What does that suggest? That if, for example, you were to switch from a Wi, Fi connection to your data prepare connection on the go, IKEv2 could manage that without dropping the connection. That, you need to know that IKEv2 tends to be faster than Open, VPN, however it's likewise easier to obstruct than the Open, VPN protocol.
Openvpn Vpn Protocol
Our tunneling protocol.
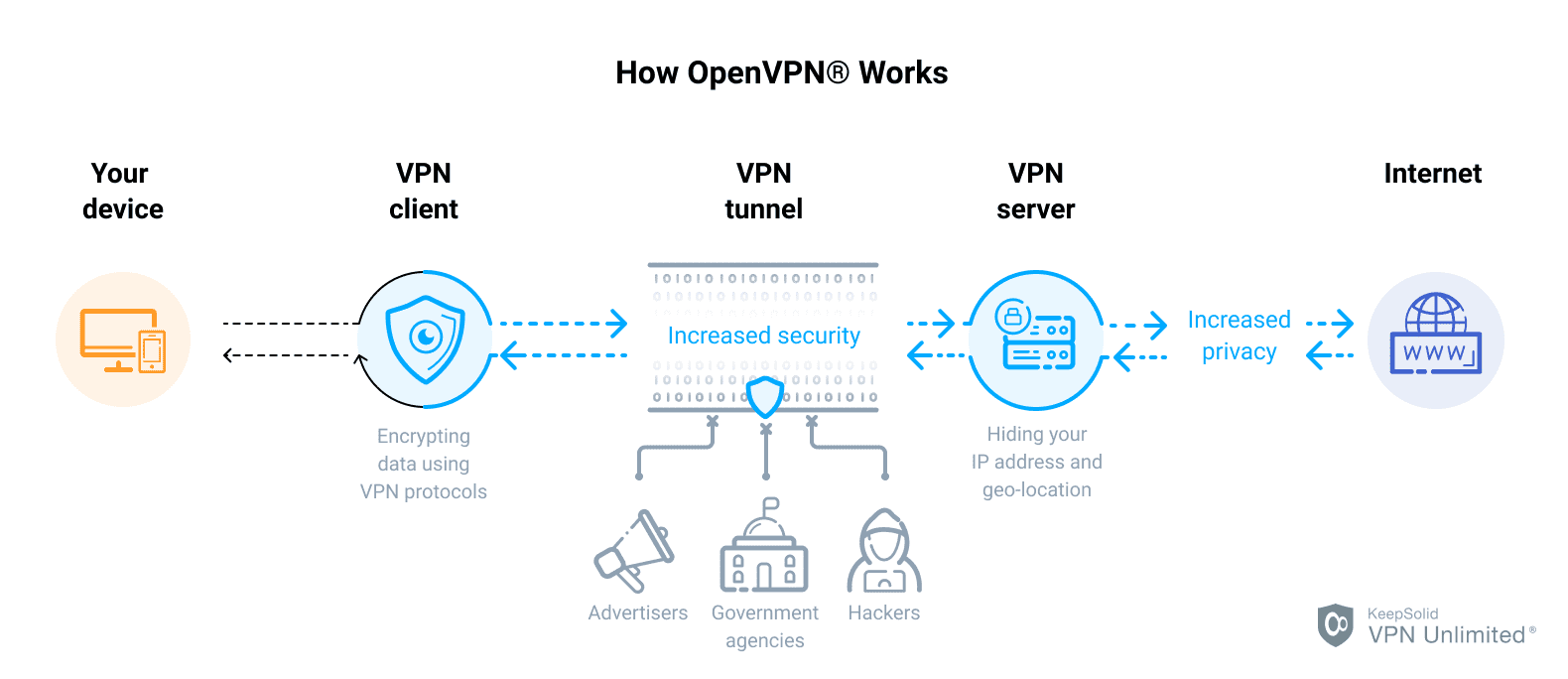
The Open, VPN Neighborhood Edition (CE) is an open source Virtual Private Network (VPN) project. It creates protected connections over the Internet using a custom security procedure that utilizes SSL/TLS. This community-supported OSS (Open Source Software application) job, utilizing a GPL license, is supported by lots of Open, VPN Inc. developers and factors as well as the prolonged Open, VPN neighborhood.

Open, VPN is an open source connection protocol used to help with a secure tunnel between 2 points in a network. In layperson's terms, this means that it is a relied on innovation utilized by numerous virtual personal networks, or VPNs, to ensure any information sent out over the web is encrypted and personal.
What Is Openvpn?
It's not unusual to go to a VPN website and see them boasting about the truth that they offer Open, VPN as a function.
You're now 100% secure online with zero risk of being hacked? Wellnot precisely. No single tool or encrypted connection to the internet can guarantee your security and personal privacy, and Open, VPN is no various. There are good reasons why it is considered one of the most secure connections, which we'll cover below.
Some of the links in this post are affiliate links, which means that at no extra expense to you, I may be compensated if you pick to utilize some of the services listed. I just suggest what I personally utilize and I hope that the free info supplies worth to you! Prior to we dive deeper into addressing the concern "what is Open, VPN" and how it works, let's take an action back to make certain we're clear on what a VPN protocol is.
What Is Openvpn & Is It A Safe Choice In 2023?
For instance, if you leave your home to head out to eat, there are particular things you will consider: the safety of the path, the right mode of transportation, what you need to take with you, and so on. Likewise, when information travels through a channel, it follows certain rules. And there isn't simply one set of rules to follow.
Perhaps you've heard of these protocols before. They generally go by an acronym such as: Point-to-point tunneling protocol Layer 2 tunneling protocol Internet crucial exchange variation 2 Secure socket tunneling protocol, What is Open, VPN when compared to each of the procedures noted above? There's actually one big difference: It is open source.
Latest Posts
5 Best Vpns For Mobile Data To Protect Your Privacy
Top Mobile Vpns For The Enterprise - Cso Online
Cisco Mobile Vpn